The Digital Shield: An Introduction to DDoS Protection and Mitigation
In the modern digital landscape, availability is everything. For any online business, government service, or financial institution, their website or application being offline means lost revenue, damaged reputation, and broken trust. One of the most common and disruptive threats to this availability is the Distributed Denial-of-Service (DDoS) attack. This is where the power of DDoS Protection and Mitigation comes into play. A DDoS attack is a malicious attempt to overwhelm a target server, service, or network with a flood of internet traffic, making it unavailable to legitimate users. Protection and mitigation solutions are a specialized set of technologies and services designed to detect these attacks in real-time and filter out the malicious traffic while allowing legitimate user traffic to pass through. This digital shield is an essential component of modern cybersecurity, ensuring that online services remain resilient and accessible even in the face of a massive digital assault.
Understanding a DDoS attack requires understanding its key characteristics. The "Distributed" part is crucial. The attack traffic doesn't come from a single source but from thousands or even millions of compromised computers, servers, and IoT devices from around the world. This network of compromised devices is known as a "botnet," and it is controlled by a single attacker. This distributed nature makes the attack difficult to block, as there is no single source IP address to filter. DDoS attacks come in several forms. Volumetric attacks, the most common type, simply aim to saturate the target's internet connection with a massive flood of traffic. Protocol attacks exploit weaknesses in network protocols to exhaust the resources of servers or firewalls. Application-layer attacks (Layer 7 attacks) are more sophisticated, mimicking legitimate user traffic to overwhelm a specific application, such as a web server.
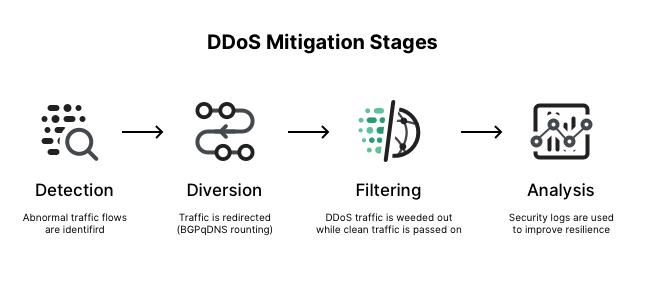
A DDoS protection and mitigation solution works by acting as a filter or "scrubbing center" for an organization's internet traffic. The process involves several key stages. The first is detection. The solution continuously monitors the traffic flowing to the organization's network, looking for anomalies that indicate the start of a DDoS attack, such as a sudden, massive spike in traffic volume or a large number of requests from unusual sources. Once an attack is detected, the traffic is diverted. This means all of the organization's internet traffic, both good and bad, is re-routed to the mitigation provider's specialized global network, which has massive capacity and is designed to absorb these large-scale attacks. The attack traffic never even reaches the organization's own internet connection, preventing it from being saturated.
The heart of the solution is the mitigation or "scrubbing" process. Inside the provider's globally distributed scrubbing centers, the diverted traffic is passed through a series of sophisticated filters and analysis engines. These systems are designed to distinguish between malicious attack traffic generated by bots and legitimate traffic from real users. The attack traffic is identified and dropped, while the clean, legitimate traffic is allowed to pass through. This "clean" traffic is then forwarded back to the organization's network and its web servers. To the end-user, the process is seamless and invisible. They are able to access the website or application as normal, completely unaware that a massive DDoS attack is being fought off in the background. This ability to absorb and filter malicious traffic at scale is the core value of any DDoS mitigation solution.
Top Trending Reports:
- Art
- Causes
- Crafts
- Dance
- Drinks
- Film
- Fitness
- Food
- Spiele
- Gardening
- Health
- Startseite
- Literature
- Music
- Networking
- Andere
- Party
- Religion
- Shopping
- Sports
- Theater
- Wellness